If you want to know how to hack a WiFi router, just read this step by step instructions How to use aircrack-ng, follow a series of proven commands and easily crack your WiFi password.
Using these commands you can hack a WiFi router with WPA/WPA2-PSK (pre-shared key) encryption.
The basis of this WiFi hacking technique is to intercept the WPA/WPA2 handshake during authentication and crack the PSK using aircrack-ng.
They can be interesting when you know Essen but don't have Handshake yet, so unlike a classic attack, you can time them and save valuable time when using them. In this case, we are dealing with an indirect attack, where we see the target and prepare the ground.
Configuring the map in monitoring mode
Please note: Passwords less than 8 or more than 63 characters will be considered invalid. Do a full scan to fix any errors. Start creating the table. And finally, admire the speed of the hack. It only requires your computer. If the card is displayed in the list, it can be included in monitoring mode. To enable it into monitoring mode, you must run the following command.
How to hack WiFi - basic steps:
- Install the latest version of aircrack-ng
- Put your wireless network interface into monitoring mode using airmon-ng
- Run airodump-ng to intercept handshake on AP channel with BSSID filtering
- [Optional] Use aireplay-ng to de-authenticate the client
- Run aircrack-ng to crack WPA/WPA2-PSK using intercepted handshake
1. Aircrack-ng: Download and Install
Latest Version Only: If you really want to hack WiFi, you should not install outdated aircrack-ng from your operating system repository. Download and compile the latest version yourself.
To do this, run the following command. To do this, open a new terminal and run the following command. To crack the key, run the following command. Did you like this lesson? Help us improve the site! So share it with your friends! This lesson is thus a big blow. This tutorial has three parts.
We stimulate the target network: by passing through to authorized equipment, we force the target access point to “talk” to our machine. It is at this stage that we will determine the network whose key we want to discover. . The GUI then loads and you can change the keyboard layout if needed, with flags located in the bottom right corner of the screen, next to the time. All of these commands must be entered into a terminal on the attacking computer. In each command line, the fixed parts are in bold, the parts that do not need to be adapted to each attack.
Install the required dependencies:
$ sudo apt-get install build-essential libssl-dev libnl-3-dev pkg-config libnl-genl-3-dev
Download and install the latest version of aircrack-ng (current version):
$ wget http://download.aircrack-ng.org/aircrack-ng-1.2-rc4.tar.gz -O - | tar -xz $ cd aircrack-ng-1.2-rc4 $ sudo make $ sudo make install
Make sure it is installed exactly latest version aircrack-ng:
Orders must be made in item order. To access the terminal, you can use the dedicated icon on the taskbar. To complete this tutorial, you will need three terminal windows. This part displays the surrounding networks, selects a target, and begins collecting packets. Commands must be entered in a terminal window.
So this is the ID I'll have to use. This applies to me here, but it may be different for you. As announced in the preamble, this tutorial requires that at least one device be connected to the network whose key is being requested.
$ aircrack-ng --help Aircrack-ng 1.2 rc4 - (C) 2006-2015 Thomas d'Otreppe http://www.aircrack-ng.org
2. Airmon-ng: Monitoring Mode
Now you need to put the wireless network interface into monitoring mode.Monitoring mode allows a computer with a wireless network interface to monitor all traffic on the wireless network.
What is especially important for us is that the monitoring mode allows you to intercept all transmitted packets without directly connecting to any WiFi router.
We use the information received previously. Before you can run packet capture, you will have to interrupt scanning for incomplete networks. The key indicator for a crack is the number of data packets collected. This part is optional, but without it the crack may take several hours to complete. Run these commands in a new terminal window. Optional, this step allows a legitimately connected computer to pass. There are other distributions as well. Even if there are ways to enter packets without stations, they are on the one hand more complex, but also have a lower success rate, so we will more accurately detail the method with a more reliable station.
Find and stop all processes that may interfere:
$ sudo airmon-ng check kill
Start the wireless interface in monitoring mode:
$ sudo airmon-ng start wlan0 Interface Chipset Driver wlan0 Intel 6235 iwlwifi - (monitor mode enabled on mon0)
In the above example, airmon-ng created a new wireless interface mon0 and switched it to monitoring mode.
So mon0 is the correct interface name that we will use later in this tutorial.
Okay, we'll get back to the heart of the matter for a bit now. Get indentation. Burn the giveaway on a good cake set the side for 2 seconds. Then you are taken to this screen. To do this: Right-click the American flag icon in the lower right corner and then select French.
Here we see that the card is correctly recognized and that monitor mode is directly activated. Monitor mode allows you to collect all packets that pass through those that are not addressed to you. If you have atheros management on chipset cards it's a bit different, even with one card you can create multiple virtual cards. From now on, you will use this interface for all the following commands. The first part corresponds to access points, and the second part to stations.
3. Airodump-ng: Handshake Interception
Useful advice: Want to have a little "fun"? Create a fork bomb in Linux! One small line that can hang the entire system!
Now that the wireless adapter is set to monitor mode, we have the opportunity to see all the traffic passing by us.
This can be done using the airodump-ng command:
We will first ping the access point with a "-1" "fake authentication" attack. It's possible if you don't capture the signal very well that successful authentication and merging are not instantaneous. And here's an example that's short, but you can easily have 40 rows.
We modify and simply add a few parameters. This file is located in the directory from which you started the broadcast. It is these arps that allow us to influence traffic by reintroducing them. Don't forget to put yourself in the same directory. To avoid typing as the syntax is almost the same as with the -1 option, click on the up arrow to find what you previously entered.
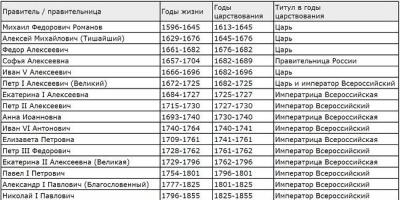
$ sudo airodump-ng mon0
All visible access points are shown at the top of the screen, and connected clients at the bottom:
CH 1 ][ Elapsed: 20 s ][ 2014-05-29 12:46 BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 00:11:22:33:44:55 -48 212 1536 66 1 54e WPA2 CCMP PSK CrackMe 66:77:88:99:00:11 -64 134 345 34 1 54e WPA2 CCMP PSK SomeAP BSSID STATION PWR Rate Lost Frames Probe 00:11:22:33:44:55 AA:BB:CC :DD:EE:FF -44 0 - 1 114 56 00:11:22:33:44:55 GG:HH:II:JJ:KK:LL -78 0 - 1 0 1 66:77:88:99: 00:11 MM:NN:OO:PP:QQ:RR -78 2 - 32 0 1
Therefore, it is advisable to start the first air filter, of which one packet is 300k. If the key is supposed to be 64 bits. La, just let it spin and the key should appear even if the crack is working. And after a short wait.
Of course, you can combine with the fiction factor. Here we will talk about wires, previously ethereal, the screens were made with ethereal, there may be slight differences. In most cases this is. To display only those that interest you, apply a filter in the filter window.
Preparing the environment
Install necessary tools.
Listening to the network interface
Important: select a network with connected clients. Discovery of the dedicated network interface created by this command. Check packet injection for the selected network. If the injection works, you should get the following result.In order to catch the handshake, determine the access point you are interested in and run airodump-ng on the same channel filtered by BSSID:
$ sudo airodump-ng -c 1 --bssid 00:11:22:33:44:55 -w WPAcrack mon0 --ignore-negative-one Now we just have to wait for airodump-ng to catch the handshake.
If you want to speed up this process, go to step #4 and try to force the connected wireless client to reconnect to the router.
If you're interested, take a look at this. Then you will need to grab the packages, click the "play" icon in the top left corner of the window. Another will open small window, then click Start Scan, then select the network you want and click Capture. Then save wherever you want. Now let's open a shell and give it root and start changing the attributes of our network card, putting it in monitoring mode, that is, "so that it can receive all the data from other networks and has a chance" to input packets from us to other tabs and enter.
All good Okay, we start looking around and run the next command. Now open on one shell, the screen and in a few seconds, if nearby networks appear nearby with their names and many other data that we will need later. Here's the screen as it appears.
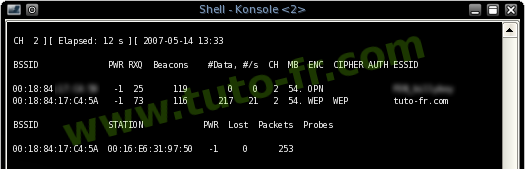
After some time has passed, you should see the message WPA handshake: 00:11:22:33:44:55 in the upper right corner of the screen.
This message means that airodump-ng successfully intercepted the handshake:
CH 1 ][ Elapsed: 45 s ][ 2014-05-29 13:15 WPA handshake: 00:11:22:33:44:55 BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 00:11 :22:33:44:55 -48 212 1536 66 1 54e WPA2 CCMP PSK CrackMe BSSID STATION PWR Rate Lost Frames Probe 00:11:22:33:44:55 AA:BB:CC:DD:EE:FF -44 0 - 1 114 56
If you do not have signal strength, you can estimate it from the beacon number: the larger the beacon, the better quality signal. Intermediate values represent mixed values. Bottom block of data of detected clients. Some drivers do not report packages. The number of data fragments received. Network names discovered by this client. Only after capturing the victim's handshake.
We become the Root, now if we came here we should know it. We go most specifically and after selecting the target we will parse the same and save in a file the handshake packets that we will use to find the password we enter.
4. Aireplay-ng: Client Deauthentication
If you don't want to wait for airodump-ng to intercept the handshake, you can try sending a message to the client yourself, saying that it is no longer connected to the access point.
After this, there is a chance that the wireless client will try to reconnect and we will be able to intercept the handshake.
This article is for didactic purposes, doing this on networks where you don't have permission is illegal. It has many variations, some specific to specific attacks and more general ones. To understand which interface is free in order to be able to change and start network monitoring.
If the program has errors, just enter. And repeat the command earlier. Start recording data that is transmitted for the designated network. And here is the key, and it took about 2 minutes to decrypt it. The slowest step is data interception, depending on how much the device receives it will be more or less long. Using another computer, go through the steps and try to understand each step, perhaps by trying other ways or methods and learning the tools that are deeply embedded.
Send broadcast deauth message:
$ sudo aireplay-ng --deauth 100 -a 00:11:22:33:44:55 mon0 --ignore-negative-one
Send a targeted deauth message (the attack is more effective when aimed at a specific client):
$ sudo aireplay-ng --deauth 100 -a 00:11:22:33:44:55 -c AA:BB:CC:DD:EE:FF mon0 --ignore-negative-one
Useful advice: Need to hack your WiFi password? Don't waste your time! Use "John the Ripper" - the fastest password cracker!
More recent versions of software and documentation are available on the official website. Alternatively, it could be a firmware issue. You can activate all 14 channels with the following commands. Which best card for purchase? This is a list of recommended cards.
First of all, make sure your card is compatible and the correct driver is installed. Network card type. Channel number, between 1 and you can also specify 0 to scan all channels. Prefix for the output file. Also, the capture file can be empty. The cause of the error is unknown. It is planned not to bring them to other platforms. This is because your driver does not drop packed packets.
5. Aircrack-ng: Hack WiFi Password
Unfortunately, there is no way to break WPA/WPA2-PSK encryption other than using brute force.To hack WiFi, you need a dictionary with passwords to enumerate.
The main thing to remember is that this hacking method is only as good as your password dictionary.
Some dictionaries can be downloaded from here.
Each access point sends about 10 frames per second at the slowest rate, so they can be detected at a good distance. # Data The number of packets captured, including broadcast data packets. The dot indicates short preamble support.
The screenshot above shows 2 clients. How to join multiple capture files? This is a list of options. You must sniff until there is a handshake between the wireless client and the access point. This simple circuit, is likely to be broken by a statistical attack, since the first bytes of the encrypted message are strongly associated with the shared key.
Run the following command to crack WPA/WPA2-PSK:
$ aircrack-ng -w wordlist.dic -b 00:11:22:33:44:55 WPAcrack.cap Aircrack-ng 1.2 beta3 r2393 548872 keys tested (1425.24 k/s) KEY FOUND! [ 987654321 ] Master Key: 5C 9D 3F B6 24 3B 3E 0F F7 C2 51 27 D4 D3 0E 97 CB F0 4A 28 00 93 4A 8E DD 04 77 A3 A1 7D 15 D5 Transient Key: 3A 3E 27 5E 86 C3 01 A8 91 5A 2D 7C 97 71 D2 F8 AA 03 85 99 5C BF A7 32 5B 2F CD 93 C0 5B B5 F6 DB A3 C7 43 62 F4 11 34 C6 DA BA 38 29 72 4D B9 A3 11 47 A6 8F 90 63 46 1B 03 89 72 79 99 21 B3 EAPOL HMAC: 9F B5 F4 B9 3C 8B EA DF A0 3E F4 D4 9D F5 16 62
Currently, the only vulnerability is a dictionary attack, which is useless against a well-constructed passphrase. If all the voices are the same or there are many negatives, then the capture file is damaged or the key is not static. The fake result prevents you from finding the key. How to extract a captured file? This software is experimental, so it may or may not work depending on the service pack level.
You can also update the firmware. All drivers need a patch to support injection in monitor mode. In this case, compile a new kernel, install it, and reboot. Then try to compile the drivers. In this case, set the automatic reset interval.
Useful advice: Cracking a password often takes a long time. Combine aircrack-ng with “John The Ripper” to be able to pause the brute force without losing your current progress!
The last few years have seen the rise of wireless technology. Wi-Fi networks (802.11a/b/g standard networks) are becoming increasingly popular, and if earlier it was mainly about the use of wireless networks in offices and hot spots, now they are widely used both at home and for deploying mobile phones. offices (offices during business trips). Wireless access points and SOHO class wireless routers are sold especially for home users and small offices, and pocket wireless routers are sold for mobile users. However, when deciding to switch to a wireless network, it should be remembered that at the current stage of development it has one significant drawback - imperfection in terms of security. In this article we will talk about the most vulnerable areas of wireless networks and show with practical examples how they are hacked. The knowledge gained can be successfully used to audit the security of wireless networks, which will allow you to avoid traditional mistakes made when deploying wireless networks. We'll first look at the basic security measures used to protect wireless networks today, and then talk about how they can be overcome by attackers.
You are pretty close to the access point. The driver has a patch and is installed correctly. However, most access points are not vulnerable. Some may appear vulnerable at first, but reject packets with less than 60 bytes. Small and medium-sized enterprises are targeted by criminals because they have fairly standard credentials. It is useful to know, at least initially, the most common attack methods.
B: We remember that these practices are illegal and therefore punishable. For more information, please refer to the article about Yus friends' computer crimes on the Internet. The purpose of this article is purely informative. Therefore, we do not accept any responsibility for any damage you may cause.
Wireless Security Methods
The 802.11a/b/g wireless network standards provide several security mechanisms:
- WEP (Wired Equivalent Privacy) authentication and data encryption mode;
- WPA (Wi-Fi Protected Access) authentication and data encryption mode;
- filtering by MAC addresses;
- using hidden network ID mode.
WEP protocol
All modern wireless devices (access points, wireless adapters and routers) support the WEP security protocol, which was originally included in the IEEE 802.11 wireless network specification.
The WEP protocol allows you to encrypt the transmitted data stream based on the RC4 algorithm with a key size of 64 or 128 bits. Some devices also support keys of 152, 256 and 512 bits, but this is rather the exception to the rule. The keys have a so-called static component of 40 and 104 bits in length, respectively, for 64- and 128-bit keys, as well as an additional dynamic component of 24 bits in size, called the Initialization Vector (IV).
At the simplest level, the WEP encryption procedure is as follows. Initially, the data transmitted in the packet is checked for integrity (CRC-32 algorithm), after which the checksum (Integrity Check Value, ICV) is added to the service field of the packet header. Next, a 24-bit initialization vector (IV) is generated, to which a static (40- or 104-bit) secret key is added. The 64- or 128-bit key thus obtained is the initial key for generating the pseudo-random number used to encrypt the data. Next, the data is mixed (encrypted) using the logical XOR operation with a pseudo-random key sequence, and the initialization vector is added to the frame service field.
On the receiving side, the data can be decrypted, since information about the initialization vector is transmitted along with it, and the static component of the key is stored by the user to whom the data is transferred.
The WEP protocol provides two methods of user authentication: Open System (open) and Shared Key (shared). With open authentication, no authentication actually occurs, meaning any user can gain access to the wireless network. However, even in case open system WEP data encryption is allowed.
WAP protocol
In 2003, another security standard was introduced - WPA, the main feature of which is the technology of dynamic generation of data encryption keys, built on the basis of the TKIP (Temporal Key Integrity Protocol), which is a further development of the RC4 encryption algorithm. Under the TKIP protocol, network devices work with a 48-bit initialization vector (as opposed to the 24-bit WEP vector) and implement rules for changing the sequence of its bits, which eliminates key reuse. The TKIP protocol provides for the generation of a new 128-bit key for each transmitted packet. In addition, cryptographic checksums in WPA are calculated using a new method - MIC (Message Integrity Code). Each frame contains a special eight-byte message integrity code, the verification of which allows you to repel attacks using forged packets. As a result, it turns out that each data packet transmitted over the network has its own unique key, and each wireless network device is endowed with a dynamically changing key.
In addition, the WPA protocol supports encryption using the advanced AES (Advanced Encryption Standard) standard, which has a more secure cryptographic algorithm compared to the WEP and TKIP protocols.
When deploying wireless networks at home or in small offices, a variant of the WPA security protocol based on shared keys - WPA-PSK (Pre Shared Key) - is usually used. In the future, we will consider only the WPA-PSK option, without touching on the WPA protocol options aimed at corporate networks, where user authorization is carried out on a separate RADIUS server.
When using WPA-PSK, a password of 8 to 63 characters is specified in the access point settings and client wireless connection profiles.
MAC Address Filtering
MAC address filtering, which is supported by all modern access points and wireless routers, although not integral part The 802.11 standard is nevertheless considered to improve the security of a wireless network. To implement this function, a table of MAC addresses of wireless adapters of clients authorized to work in this network is created in the access point settings.
Hidden SSID Mode
Another precaution often used in wireless networks is the hidden network identifier mode. Each wireless network is assigned a unique identifier (SSID), which is the name of the network. When a user tries to log into a network, the wireless adapter driver first scans the airwaves for the presence of wireless networks. When using the hidden identifier mode (as a rule, this mode is called Hide SSID), the network is not displayed in the list of available ones and you can connect to it only if, firstly, its SSID is precisely known, and secondly, a profile has been created in advance connections to this network.
Hacking wireless networks
Having familiarized ourselves with the main methods of protecting 802.11a/b/g networks, we will consider ways to overcome them. Note that the same tools are used to hack WEP and WPA networks, so first we will tell you what is included in the attacker’s arsenal.
First of all, we need a laptop with a wireless adapter. The main problem that arises in the process of selecting wireless hacking tools is ensuring compatibility between the wireless adapter chip used software, and the operating system.
Selecting a wireless adapter
The fact is that most utilities that allow you to hack wireless networks are “tailored” for Linux systems. There are versions of some utilities for Windows XP. However, depending on the wireless adapter chip, certain wireless cards can be used with utilities for both Linux and Windows XP systems, and some wireless adapters can be used with utilities only for Linux or only for Windows XP systems. There are wireless adapters that are not supported by either Linux or Windows XP utilities. In addition, there are chips that, although supported by utilities, work extremely slowly (in terms of capturing and analyzing packets).
The fact is that to perform the task of hacking wireless networks, special (non-standard) drivers for wireless network adapters are required. The standard modes of any wireless adapter are Infrastructure (Basic Service Set, BSS) and ad-hoc (Independent Basic Service Set, IBSS). In Infrastructure mode, each client is connected to the network through an access point, and in ad-hoc mode, wireless adapters can communicate with each other directly, without using an access point. However, both of these modes do not allow the wireless adapter to listen on the air and intercept packets. In both cases, the network adapter will catch packets that are intended only for the network for which it is configured. In order to be able to see other networks (having a hidden ESSID) and capture packets, there is a special monitoring mode (Monitor mode), when switched to which the adapter is not associated with any specific network and catches all available packets. Typically, the drivers supplied by the wireless adapter manufacturer do not support monitoring mode, and in order to enable it, you must install special drivers, often written by a group of third-party developers. It should be immediately noted that for Windows operating systems such special drivers exist only for wireless adapters based on Hermes, Realtek, Aironet and Atheros chips. Driver support for this mode for operating systems of the Linux/BSD family is largely determined by the openness of the specifications for the card, however, the list of supported devices is much wider than for the Windows family. Drivers for Linux/BSD systems with support for monitoring mode can be found for wireless adapters based on the following chipsets: Prism, Orinoco, Atheros, Ralink, Aironet, Realtek, Hermes and Intel, although drivers based on Intel chips are not suitable for all devices.
Currently, all laptops based on Intel Centrino mobile technology have built-in wireless adapters based on Intel chips (IPW2100, IPW2200, IPW2915, IPW3945 chips), but for our purposes these adapters are not suitable - although they are compatible with Linux utilities. used for hacking, these chips work extremely slowly, and are generally incompatible with Windows utilities.
Selecting an operating system
Regarding the choice of operating system, the following recommendations can be given. Linux systems are more preferable for these purposes, since when using Linux a set possible tools much wider, and Linux utilities work much faster. But this does not mean that you cannot use Windows XP together with Windows utilities. In the future, we will consider both options for hacking wireless networks - that is, using both Linux and Windows utilities. At the same time, we understand perfectly well that not all users are in a hurry to switch from Windows to Linux. Despite all its shortcomings, Windows OS is much more widespread, and it is much easier to learn for a novice user. Therefore, in our opinion, the optimal option is to use Windows XP as the main operating system on a laptop, and for tasks of hacking a wireless network - Linux Live CD, which runs from a CD and does not require installation on the computer’s hard drive. The best solution in our case there will be a BackTrack disk, which is built on the Linux OS (kernel version 2.6.18.3) and contains all the necessary tool packages for hacking networks. An image of this disk can be downloaded from the website using the link: http://www.remote-exploit.org/backtrack.html.
Software set
Traditionally, to hack wireless networks, the aircrack software package is used, which exists in versions for both Windows XP (aircrack-ng 0.6.2-win) and Linux (aircrack-ng 0.7). This package is distributed absolutely free of charge and can be downloaded from the official website www.aircrack-ng.org. There is simply no point in looking for any other utilities, since this package is the best solution in its class. In addition, it (the Linux version, of course) is included in the BackTrack disk.
Hacking Wireless Networks Using a BackTrack Live CD
So, no matter what operating system you have installed on your laptop, we will use the BackTrack boot disk to hack the wireless network. Note that in addition to the tools we need to hack a wireless network, this disk contains many other utilities that allow you to audit networks (port scanners, sniffers, etc.). By the way, such a disk is useful for any system administrator involved in network auditing.
Hacking any wireless network using the BackTrack disk is performed in three stages (Table 1):
- collecting information about the wireless network;
- packet capture;
- packet analysis.
The first step is to collect detailed information about the wireless network that is being hacked: the MAC addresses of the access point and the active client of the wireless network, the name of the network (network ID) and the type of encryption used. To do this, use the airmon-ng, airodump-ng and Kismet utilities - the first of them is necessary to configure the wireless network adapter driver to monitor the wireless network, and the other two allow you to obtain the necessary information about the wireless network. All of these utilities are already included on the BackTrack disk.
Table 1. Steps to hack a wireless network using the BackTrack Live CD
|
Stage number |
Description |
Utilities used |
Result |
|
|
Collecting wireless network information |
airmon-ng airodump-ng Kismet |
Access point MAC address, active client MAC address, network type, network ID, encryption type (WEP, WPA-PSK), communication channel number |
||
|
Packet interception |
airodump-ng Kismet airoplay-ng |
|||
|
Packet analysis |
Key selection |
Password selection |
||
The next step is to capture packets using the airodump-ng utility. In the case where WEP encryption is used on the network, it is necessary to collect IV packets containing initialization vectors. If the traffic on the network is low (for example, the client is inactive), then you can additionally use the airoplay-ng utility to increase traffic between the client and the access point.
If the network uses WPA-PSK encryption, then it is necessary to collect packets that contain information about the client authentication procedure on the network (handshake procedure). In order to force the client to undergo authentication on the network, you can use the airoplay-ng utility to initiate the process of forcibly disconnecting it from the network and then restoring the connection.
On last stage The intercepted information is analyzed using the aircrack-ng utility. In the case of WEP encryption, the probability of guessing the key depends on the number of collected IV packets, and WPA-PSK encryption depends on the dictionary used to guess the password.
Practical examples
After brief description let's look at the procedures for hacking a wireless network practical examples With detailed description each stage and utilities used.
In our case, we were dealing with an experimental network consisting of a D-Link DWL-7000AP access point and a network client with a Gigabyte GN-WPEAG wireless PCI adapter.
To hack the network, we used a laptop with a Gigabyte GN-WMAG wireless PCMCIA adapter based on the Atheros chip. Note that when using the BackTrack disk, no additional drivers are required for the Gigabyte GN-WPEAG adapter - everything is already on the disk.
Stage 1. Collecting information about the wireless network
So, at the first stage we need to collect information about the wireless network. We insert the wireless adapter into the laptop and load the operating system from the CD. Then call the console and launch the airmon-ng utility, included in the aircrack-ng package.
This utility allows you to determine the available wireless interfaces and assign the network monitoring mode to one of the available interfaces.
The syntax for using the airmon-ng command is as follows:
airmon-ng
where are the options
Initially, the airmon-ng command is specified without parameters, which allows you to get a list of available wireless interfaces. For example, in our case, the response to the airmon-ng command was as follows:
Usage:airmon-ng
Interface Chipset Driver
wifi0 Atheros madwifi-ng
ath0 Atheros madwifi-ng VAP (parent: wifi0)
Selecting wifi0 as the wireless interface, enter the command airmon-ng start wifi0. As a result, we get another interface ath1, which is in monitoring mode (Fig. 1).
Rice. 1. Setting the wireless network monitoring mode
Next, you need to run the airodump-ng utility, which is used both to capture packets in 802.11 wireless networks and to collect information about the wireless network. The syntax for using the command is as follows:
airodump-ng
Possible command options are shown in the table. 2.
Table 2. Possible options for the airodump-ng command
|
Possible meaning |
Description |
|
|
Save only IV packets |
||
|
Use GPS daemon. In this case, the coordinates of the receiving point will also be recorded |
||
|
Write (or -w) |
File name |
Specifying the name of the file to be recorded. If you specify only the file name, it will be saved in the program’s working directory |
|
Record all packets without filtering |
||
|
Channel number (1 to 11) |
Specifying the channel number. By default, all channels are listened to. |
|
|
Specifying the 802.11a/b/g protocol |
In our case, the ath1 interface is set to monitoring mode.
However, so far we do not have information about the type of network (802.11a/b/g), the type of encryption on the network, and therefore we do not know which packets need to be intercepted (all or only IV packets). Therefore, initially you should not use options in the airodump-ng command, but only need to specify the interface - this will allow us to collect the necessary information about the network.
Thus, at the first stage we launch the airodump-ng command using the following syntax:
airodump-ng ath1
This will allow us to obtain the necessary information about the network, namely:
- MAC address of the access point;
- Client MAC address;
- network type;
- network ESSID;
- encryption type;
- communication channel number.
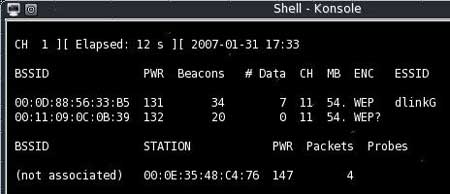
In our example, by entering the airodump-ng ath1 command, we were able to determine all the necessary network parameters (Fig. 2):
Rice. 2. Gathering information about the network
using the airodump-ng utility
- The MAC address of the access point is 00:0D:88:56:33:B5;
- Client MAC address - 00:0E:35:48:C4:76
- network type - 802.11g;
- Network ESSID - dlinkG;
- encryption type - WEP;
- communication channel number - 11.
Note that the airodump-ng utility allows you to determine the network identifier (ESSID) regardless of whether the access point is set to Hidden SSID mode or not.
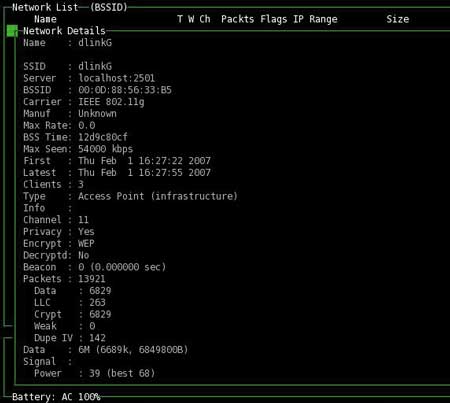
To collect information about the network, you can also use the Kismet utility included in the BackTrack disk - unlike airodump-ng, it allows you to collect much more information about the wireless network and in this sense is a complete and best-in-class wireless network analyzer. This utility has a graphical interface (Fig. 3), which greatly facilitates working with it.
Rice. 3. Gathering information about the network
using the Kismet utility
Stage 2: Packet interception
Once detailed information about the wireless network has been collected, you can begin intercepting packets using the same utilities that were used to collect information about the network - airodump-ng or Kismet. However, in this case we will need a slightly different command syntax.
WEP encryption
First, let's consider the option when the network uses WEP encryption. In this case, we need to filter only packets with an initialization vector (IV packets) and write them to a file, which will later be used to select a key.
For example, if it is known that the attacked network is an 802.11g network, it uses WEP encryption and transmission is carried out on channel 11, then the command syntax for intercepting packets could be as follows:
airodump-ng --ivs –w dump --band g --channel 11 ath1
In this example, we write only IV packets to a file called dump. The probability of successful key selection depends on the number of accumulated IV-packets and the length of the key. As a rule, with a key length of 128 bits, it is enough to accumulate about 1-2 million IV packets, and with a key length of 64 bits - on the order of several hundred thousand packets. However, the length of the key is unknown in advance and no utility can determine it. Therefore, for analysis it is desirable to intercept at least 1.5 million packets. In Fig. Figure 4 shows an example of capturing 1,137,637 IV packets in the airodump-ng utility.
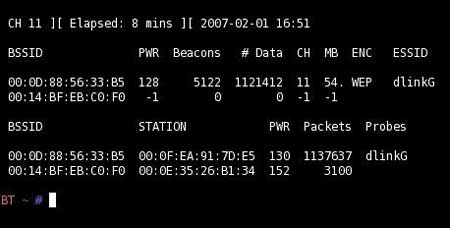
Rice. 4. Capture packets using the airodump-ng utility
The number of packets captured is interactively displayed in the airodump-ng utility, and to stop the packet capture process you just need to press the Ctrl+C key combination.
The Kismet utility can also be used to capture packets. Actually, the interception process begins immediately after the utility is launched, and recording is made to a file with the dump extension, which is saved in the working directory of the program. However, unlike the airodump-ng utility, in this case it is impossible to filter only IV packets and set the communication channel number. Therefore, when using the Kismet utility, the efficiency (accumulation rate) of packets is lower, and the number of packets that need to be intercepted should be greater than when using the airodump-ng utility.
Often, when intercepting packets, a situation arises when there is no intensive traffic exchange between the access point and the client, therefore, in order to accumulate the number of packets required for successful network hacking, you have to wait a very long time. However, this process can be accelerated by forcing the client to communicate with the access point using the aireplay-ng utility (Fig. 5). This utility is launched in parallel with the airodump-ng utility, for which you need to launch another console session.
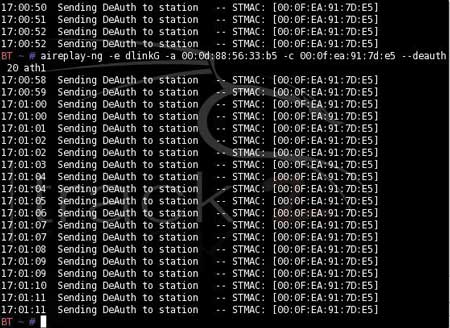
Rice. 5. Using the aireplay-ng utility to initialize traffic
between access point and client
The command syntax is as follows:
airplay-ng
This team has a very a large number of various options, which can be viewed by running the command without parameters.
For our purposes, the command syntax will look like this:
aireplay –ng -e dlinkG -a 00:0d:88:56:33:b5 -c 00:0f:ea:91:7d:95 --deauth 20 ath1
In this case, the -e dlinkG option specifies the wireless network ID; parameter -a 00:0d:88:56:33:b5 - MAC address of the access point; parameter -c 00:0f:ea:91:7d:95 - client MAC address; option --deauth 20 - attack to break the connection (20 times) followed by client authentication. When a client is authenticated, the traffic between it and the access point increases sharply and the number of packets that can be intercepted increases. If necessary, you can increase the number of connection breaks or repeat this command until the required number of packets has accumulated.
WPA-PSK encryption
With WPA-PSK encryption on a wireless network, the packet interception algorithm is slightly different. In this case, we do not need to filter out IV packets, since with WPA-PSK encryption they simply do not exist, but it also makes no sense to capture all packets in a row. Actually, all we need is a small part of the traffic between the access point and the wireless network client, which would contain information about the client authentication procedure on the network (handshake procedure). But in order to intercept the client authentication procedure on the network, it must first be forcibly initiated using the aireplay-ng utility.
Therefore, with WPA-PSK encryption, the packet interception algorithm will be as follows. We open two console sessions and in the first session we run a command to force the network to disconnect followed by re-identification of the client (aireplay-ng utility, deauthentication attack), and in the second session with a pause of one or two seconds we run a command to intercept packets (airodump-ng utility ). The command syntaxes are as follows:
aireplay–ng -e dlinkG -a 00:0d:88:56:33:b5 -c 00:0f:ea:91:7d:95 -deauth 10 ath1
airodump-ng –w dump -band g -channel 11 ath1
As you can see, the syntax of the aireplay-ng command is exactly the same as for WEP encryption, when this command was used to initialize traffic between the access point and the network client (the only difference is that there are fewer deauthentication packets). The airodump-ng command syntax lacks an IV packet filter.
The process of capturing packets needs to continue for only a few seconds, since with the deauthentication attack activated, the probability of capturing handshake packets is almost one hundred percent.
Stage 3: Packet Analysis
At the last stage, the intercepted packets are analyzed using the aircrack-ng utility, which is launched in a console session. Naturally, the syntax of the aircrack-ng command is different for WEP and WPA-PSK encryption. The general command syntax is as follows:
aircrack-ng
Possible command options are presented in table. 3. Note that several files with the extension *.cap or *.ivs can be specified as files containing captured packets (capture file(s)). In addition, when hacking networks with WEP encryption, the airodump-ng and aircrack-ng utilities can be launched simultaneously (two console sessions are used). In this case, aircrack-ng will automatically update the database of IV packages.
Table 3. Possible options for the aircrack-ng command
|
Possible meaning |
Description |
|
|
1 = static WEP, 2 = WPA-PSK |
Specifies the type of attack (WEP or WPA-PSK) |
|
|
If the option is given, all IV packets with the same ESSID value will be used. This option is also used to hack WPA-PSK networks if the ESSID is not broadcast (hidden network identifier mode) |
||
|
Access point MAC address |
Selecting a network based on the access point's MAC address |
|
|
Hidden operation mode. Information is not displayed until the key is found or the key cannot be found |
||
|
For WEP networks, it limits key selection to only a set of numbers and letters |
||
|
For WEP networks, limits key guessing to only a set of hexadecimal characters |
||
|
For WEP networks, it limits key selection to only a set of numbers |
||
|
For WEP networks, specifies the beginning of the key in hexadecimal format. Used to debug the program |
||
|
Client MAC address |
For WEP networks, sets a packet filter based on the client's MAC address. -m ff:ff:ff:ff:ff:ff is used to collect all IV packets |
|
|
64 (for 40-bit key) 128 (for 104-bit key) 152 (for 128-bit key) 256 (for 232-bit key) 512 (for 488-bit key) |
For WEP networks, specifies the key length. The default key length is 104 bits |
|
|
For WEP networks, indicates the collection of IV packets that have a given key index (from 1 to 4). By default this option is ignored |
||
|
The parameter is used when cracking WEP networks - for a 104-bit key the default value is 2, for 40-bit keys - 5. A higher value of this parameter allows you to calculate keys with fewer packets, but over a longer time |
||
|
Used when hacking WEP networks. This parameter allows you to exclude specific types of korek attacks (there are 17 types of korek attacks in total) |
||
|
Used when hacking WEP networks. Disables searching for the last character in a key |
||
|
Used when hacking WEP networks. Allows searching for the last character in a key (default) |
||
|
Used when hacking WEP networks. Allows searching for the last two characters in a key |
||
|
Used when hacking WEP networks. Prohibits the use of multiple processors in SMP systems |
||
|
Used when hacking WEP networks. Allows you to use a special (experimental) type of attack to select a key. Used when standard attacks do not allow finding the key when using more than 1 million IV packets |
||
|
Path to dictionary |
During a WPA-PSK attack, specifies the path to the dictionary used |
When using WEP encryption, the main problem is that we do not know in advance the length of the key used for encryption. Therefore, you can try to try several options for the key length, which is specified by the -n parameter. If given parameter is not specified, the default key length is set to 104 bits (-n 128).
If you know some information about the key itself (for example, it consists only of numbers, or only of letters, or only of a set of letters and numbers, but does not contain special characters), then you can use the -c, -t and -h options.
In our case, we used the aircrack-ng command with the following syntax:
aircrack-ng –a 1 –e dlinkG –b 00:0d:88:56:33:b5 –c 00:0f:ea:91:7d:95 –n 128 dump.ivs.
Here, specifying the MAC address of the access point and client, as well as the network ESSID, is redundant, since only one access point and one wireless client were used. However, if there are several clients and there are several access points, then these parameters must also be specified.
As a result, we were able to find a 128-bit key in just 25 s (Fig. 6). As you can see, hacking a network based on WEP encryption is not a serious problem, but it does not always end in success. It may turn out that not enough IV packets have been accumulated to select a key.
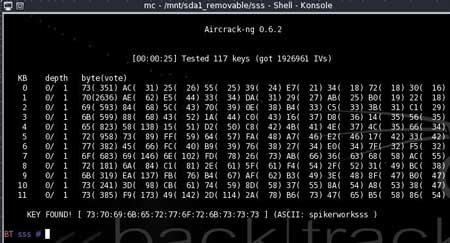
Rice. 6. Selection of a 128-bit key
using the aircrack-ng utility
WPA-PSK encryption uses the following command syntax:
aircrack-ng –a 2 –e dlinkG–b 00:0d:88:56:33:b5 –w dict dump.cap.
In this case, the probability of a positive result, that is, the probability of guessing the entire password, depends on the dictionary used. If the password is in the dictionary, it will be found. The dictionary used by the aircrack-ng program must first be mounted in the program’s working folder or the full path to the dictionary must be specified. A selection of good dictionaries can be found on the website www.insidepro.com. If they don’t help, then most likely the password is a meaningless set of characters. After all, dictionaries contain words or phrases, as well as convenient, easy-to-remember keyboard shortcuts. It is clear that there is no arbitrary set of characters in dictionaries. But even in this case there is a way out. Some utilities designed for password guessing can generate dictionaries from a given set of characters and maximum word length. An example of such a program is PasswordPro v.2.2.5.0.
However, we note once again that the probability of hacking a WPA-PSK password is very low. If the password is not specified in the form of any word, but is a random combination of letters and numbers, then it is almost impossible to guess it.
Generalization
To summarize everything that was said above about hacking wireless networks, we will once again list the main stages of this process and the commands used at each of them.
Stage 1. Gathering information about the network:
Airmon-ng start wifi0;
Airodump-ng ath1.
Stage 2. Collecting packages:
- WEP case:
Airodump-ng --ivs -w dump --band g --channel 11 ath1,
Aireplay -ng -e dlinkG -a 00:0d:88:56:33:b5 -c 00:0f:ea:91:7d:95 --deauth 20 ath1
(if there is insufficient traffic. The command is launched in a separate console session);
- WPA-PSC case:
-aireplay-ng -e dlinkG -a 00:0d:88:56:33:b5 -c 00:0f:ea:91:7d:95 --deauth 10 ath1,
Airodump-ng -w dump --band g --channel 11 ath1
(the command is run in a separate console session).
Stage 3. Packet analysis:
- WEP case:
Aircrack-ng -a 1 -e dlinkG -b 00:0d:88:56:33:b5 -c 00:0f:ea:91:7d:95 -n 128 dump.ivs;
- WPA-PSK case:
Aircrack-ng -a 2 -e dlinkG-b 00:0d:88:56:33:b5 -w dict dump.cap.
Hacking wireless networks using the aircrack-ng 0.6.2-win package and Windows XP
As we already noted at the beginning of the article, there is a version of the aircrack-ng package 0.6.2-win supported by the Windows XP operating system. Let us immediately note that the capabilities of the package are not as extensive as compared to its Linux counterpart, and therefore, if there is no strong prejudice against Linux, then it is better to use the option with the BackTrack disk.
The first thing you will have to face when using the Windows version of the aircrack-ng program is the need to replace the standard drivers from the wireless network adapter manufacturer with special drivers that support monitoring and packet interception mode. Moreover, as in the case of the Linux version of the program, the specific version of the driver depends on the chip on which the network adapter is built. For example, when using our Gigabyte GN-WMAG wireless PCMCIA adapter based on the Atheros AR5004 chip, we used driver version 5.2.1.1 from WildPackets.
The procedure for hacking a wireless network using the Windows version of the aircrack-ng package is quite simple and conceptually repeats the procedure for hacking wireless networks using the Linux version of the package. It is traditionally performed in three stages: collecting information about the network, intercepting packets and analyzing them.
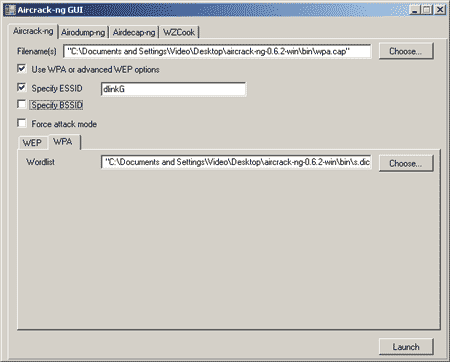
To start working with the utility, you need to run the Aircrack-ng GUI.exe file, which has a convenient graphical interface and is, in fact, a graphical shell for all the utilities included in the aircrack-ng 0.6.2-win package. The main program window (Fig. 7) has several tabs, by switching between which you can activate the necessary utilities.
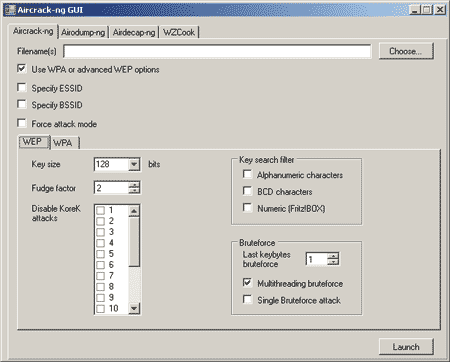
Rice. 7. Main window of the Aircrack-ng GUI utility
To collect the necessary information about the network, you need to go to the airdump-ng tab, after which the airdump-ng 0.6.2 utility will launch in a separate window.
When you run the airdump-ng 0.6.2 program (Fig. 8), a dialog box will open in which you will need to specify the wireless network adapter (Network interface index number), network interface type (o/a) chip, wireless channel number communications (Channel(s): 1 to 14, 0=all) (if the channel number is unknown, then you can scan all channels). In addition, the name of the output file in which the captured packets are stored is specified (Output filename prefix), and it is indicated whether it is necessary to capture all entire packets (CAP files) or only part of the packets with initialization vectors (IVS files) (Only write WEP IVs (y/n)). With WEP encryption, to select a secret key, it is enough to generate only an IVS file, but when using WPA-PSK encryption, you will need a cap file. By default, IVS or CAP files are created in the same directory as the airdump-ng 0.6.2 program.
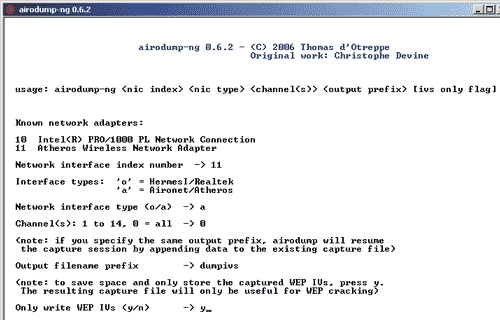
Rice. 8. Setting up the airdump-ng 0.6.2 utility
After configuring all the options of the airodump-ng 0.6.2 utility, an information window will open, which displays information about detected wireless access points, information about network clients, and statistics of intercepted packets (Fig. 9).
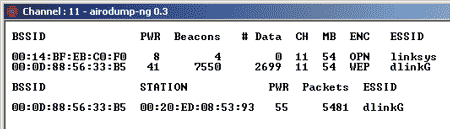
Rice. 9. Information window of the airodump-ng 0.6.2 utility
If there are several access points, statistics will be displayed for each of them.
The first step is to write down the MAC address of the access point, the SSID of the wireless network and the MAC address of one of the clients connected to it (if there are several of them). Then you need to wait until a sufficient number of packets have been intercepted. To stop the packet capture process (utility operation), use the Ctrl+C key combination. Note that the Windows version of the package does not provide methods to forcefully increase traffic between the access point and the network client (remember that the Linux version of the package provides the aireplay-ng utility for this).
The main problem when hacking WPA-PSK networks using the Windows version of the Aircrack-ng GNU 0.6.2 program is that the client initialization procedure on the network must be captured in the CAP file, that is, you will have to sit in ambush with the running airodump-ng program. Once the network client initialization procedure is captured in the CAP file, you can stop the airodump program and begin the decryption process. Actually, in this case there is no need to accumulate intercepted packets, since only packets transmitted between the access point and the client during initialization are used to calculate the secret key.
In the case of WEP encryption, after generating the output IVS file, you can begin to analyze it using the aircrack-ng 0.6.2 utility, to launch which you again need to open the main window of the Aircrack-ng GUI program on the appropriate tab and configure the aircrack-ng utility. With WEP encryption, setting up the utility consists of setting the length of the WEP key, specifying the ESSID of the wireless network, setting the MAC address of the access point, excluding certain types of attacks (RoreK attacks), setting, if necessary, the character set used for the key, and etc. All the same settings are provided here as in the case of the Linux version of this utility. The only difference is that in the Linux version all settings are specified as options on the command line, while in the Windows version a convenient graphical interface is used to configure the utility (Fig. 10).
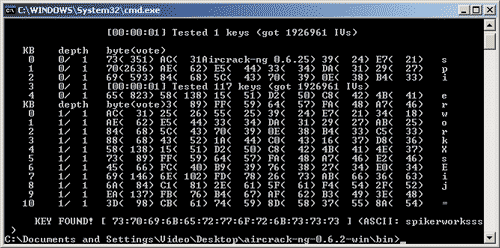
Rice. 11. Result of IVS file analysis
aircrack-ng 0.6.2 utility
The result of the IVS file analysis is shown in Fig. 11. It is unlikely that the line KEY FOUND! needs comments. Please note: the secret key was calculated in just 1 second!
When using WPA-PSK encryption in the settings of the aircrack-ng 0.6.2 utility, it is necessary to use the CAP file as the output file, and not the IVS file. In addition, you need to specify the path to the dictionary used for hacking, which is pre-installed in the directory with the aircrack-ng 0.6.2 program (Fig. 12).
Rice. 12. Result of ivs file analysis
aircrack-ng 0.6.2 utility
The result of the CAP file analysis is shown in Fig. 13. However, it should be borne in mind that a positive result of the key search is possible only if the password is present in the analyzed dictionary.
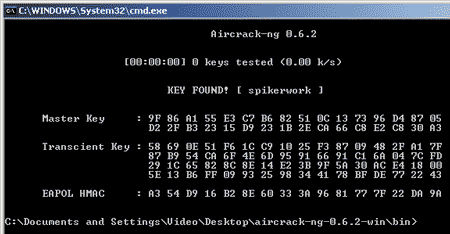
Rice. 13. Result of CAP file analysis
Bypassing MAC address filter protection
At the very beginning of the article, we noted that in addition to WEP and WPA-PSK encryption, functions such as hidden network identifier mode and MAC address filtering are often used. These are traditionally classified as wireless security features.
As we have already demonstrated with the aircrack-ng package, you cannot rely on the hidden network identifier mode at all. The airodump-ng utility we mentioned will still show you the network SSID, which can later be used to create a connection profile (unauthorized!) to the network.
Well, if we talk about such a security measure as filtering by MAC addresses, then everything is very simple here. On the Internet you can find quite a lot of different utilities for both Linux and Windows that allow you to replace the MAC address of a network interface. As an example, we can cite the following Windows utilities: SMAC 2.0 (paid utility, http://www.klcconsulting.net/smac), MAC MakeUP (free utility, www.gorlani.com/publicprj/macmakeup/macmakeup.asp - fig 14) or MAC Spoofer 2006 (free utility).
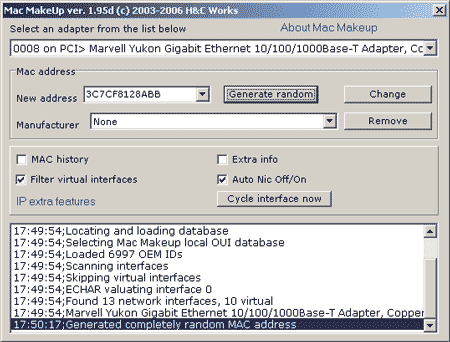
Rice. 14. MAC address spoofing using the MAC MakeUP utility
Having carried out such a substitution, you can pretend to be your own and implement unauthorized access to the wireless network. Moreover, both clients (real and uninvited) will exist quite calmly on the same network with the same MAC address, moreover, in this case the uninvited guest will be assigned exactly the same IP address as the real network client.
conclusions
So, it is not difficult to overcome the entire security system of a wireless network based on WEP encryption. Perhaps many will say that this is irrelevant, since the WEP protocol has long since died - it is not used. It has been replaced by the more robust WPA protocol. However, let's not rush to conclusions. This is true, but only partly. The fact is that in some cases, to increase the range of a wireless network, so-called distributed wireless networks (WDS) are deployed based on several access points. The most interesting thing is that such networks do not support the WPA protocol and the only acceptable security measure in this case is the use of WEP encryption. In this case, WDS networks are hacked in exactly the same way as networks based on a single access point. In addition, PDAs equipped with a wireless module also do not support the WPA protocol, so to include a PDA-based client in a wireless network, you must use the WEP protocol in it. Consequently, the WEP protocol will be in demand in wireless networks for a long time.
The examples of hacking of wireless networks that we have considered very clearly demonstrate their vulnerability. If we talk about the WEP protocol, it can be compared to foolproof protection. This is about the same as a car alarm - only it saves you from hooligans. As for such precautions as MAC address filtering and hidden network identifier mode, they cannot be considered as protection at all. Nevertheless, even such means should not be neglected, although only in combination with other measures.
The WPA protocol, although much more difficult to crack, is also vulnerable. However, do not lose heart - not everything is so hopeless. The fact is that the success of hacking a WPA secret key depends on whether it is in the dictionary or not. The standard dictionary we used is just over 40 MB in size, which is generally not that much. After three attempts, we managed to find a key that was not in the dictionary, and hacking the network turned out to be impossible. The number of words in this dictionary is only 6,475,760, which, of course, is very small. You can use dictionaries with a larger capacity, for example, on the Internet you can order a dictionary on three CDs, that is, almost 2 GB in size, but even it does not contain all possible passwords. Indeed, let's roughly calculate the number of passwords from 8 to 63 characters long that can be formed using 26 letters of the English alphabet (case sensitive), ten numbers and 32 letters of the Russian alphabet. It turns out that each symbol can be selected in 126 ways. Accordingly, if we take into account only passwords with a length of 8 characters, then the number of possible combinations will be 1268=6.3·1016. If the size of each word of 8 characters is 8 bytes, then the size of such a dictionary will be 4.5 million terabytes. But these are only combinations of eight symbols! What kind of dictionary will you get if you go through all possible combinations from 8 to 63 characters?! You don’t have to be a mathematician to calculate that the size of such a dictionary will be approximately 1.2·10119 TB.
So don't despair. There is a good chance that the password you are using is not in the dictionary. Simply, when choosing a password, you should not use words that make sense. It is best if it is a random set of characters - something like “FGproukqweRT4j563app”.